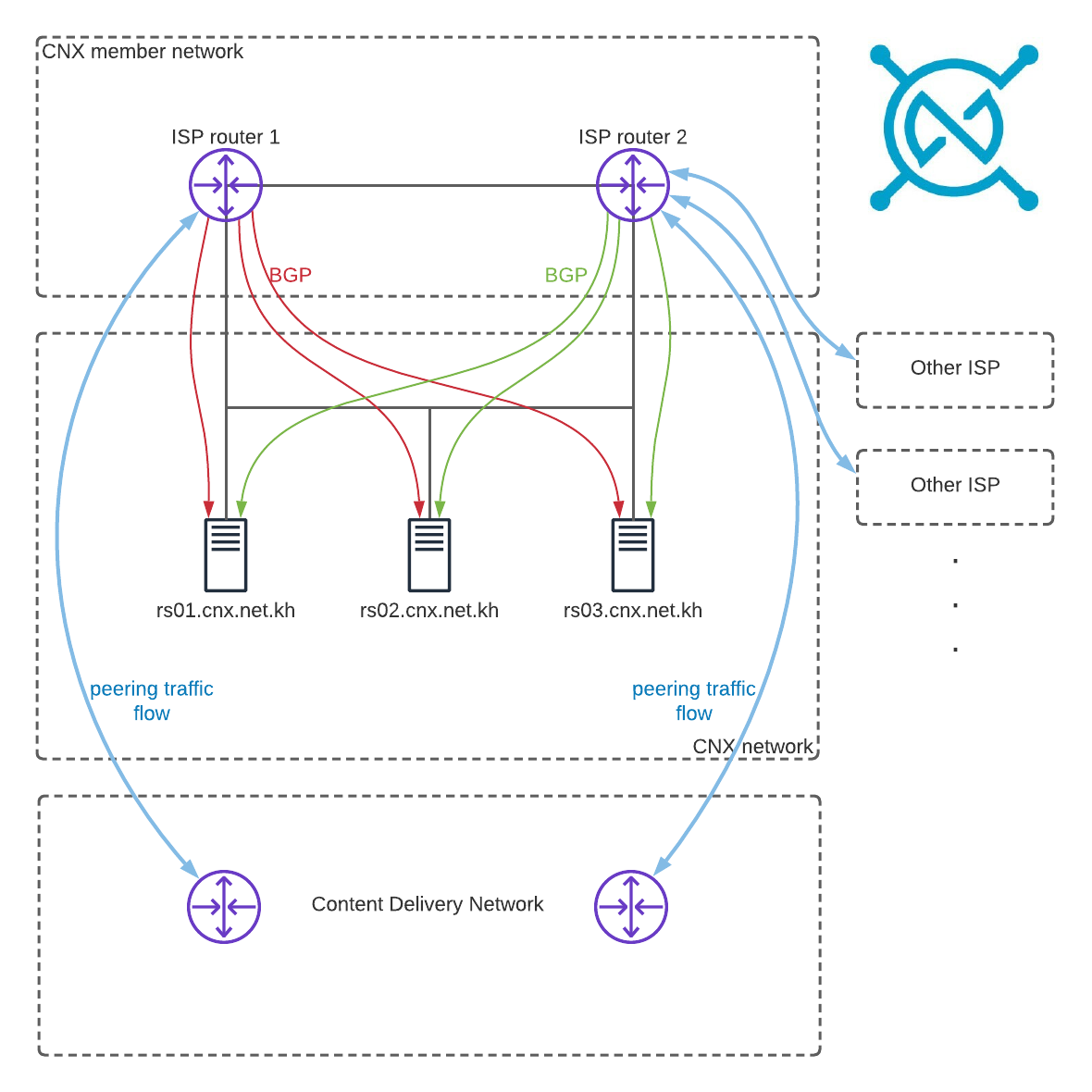
Route servers
CNX offers connected networks the opportunity to peer via its route servers, thus helping to reduce the complexity of your peering. However you should still
maintain your peering relationships and peering polices! CNX is not responsible for any impact on traffic flow due to policies configured at our route servers by other members.
Introduction
When peering at an exchange, you would normally need to maintain separate BGP sessions to each of your peers’ routers. With a route server you can replace all or a subset of these sessions with one session towards each route server. CNX operates 3 primary route-servers (RS01, RS02 & RS03), one at each Facility.
The route servers do not partake in the forwarding path, they do not forward any traffic and our ASN will not be visible in the forwarding path. Peering with a route server does not mean that you must accept routes from all other route server participants, you are free to filter routes or peers where you have a direct peering agreement.
Please contact us to setup the BGP session with our route servers.
Route Server connection diagram
Route Server details
Our route servers support IPv4, IPv6 and 4byte ASNs.
| ASN | 132213 |
| Peering Network IPv4 | 103.7.144.0/25 |
| rs01.cnx.net.kh | 103.7.144.1 |
| rs02.cnx.net.kh | 103.7.144.2 |
| rs03.cnx.net.kh | 103.7.144.3 |
| Peering Network IPv6 | 2001:DE8:1D::/64 |
| rs01.cnx.net.kh | 2001:DE8:1D::1 |
| rs02.cnx.net.kh | 2001:DE8:1D::2 |
| rs03.cnx.net.kh | 2001:DE8:1D::3 |
Other supported features: large communities, route origin validation.
Supported features that can be enabled on request: GTSM, BFD.
See the automatically generated route server policy for details on route server configuration and communities. A looking glass is available.
when peering with our RS, please note
- You must peer with all RS and advertise the same amount and length of prefixes for resilience.
- Only your own ASN and ASNs that you listed as downstream are accepted by the RS.
- You can only advertise prefixes assigned to you or your downstream peers.
- Disable check on first-ASN, this is applicable to Huawei (“undo check-first-as”) and Cisco equipment (“no bgp enforce-first-as”).
- For IPv4, CNX RS will deny all network updates with a network mask length greater than /24.
- For IPv6, CNX RS will deny all network updates with a network mask length shorter than /16 or greater than /48.
- The RS only accept a maximum count of prefixes as listed in your PeeringDB.
- The route servers are set to passive mode and will never initiate a BGP session. You should make sure that your equipment does so, i.e. connects to our TCP port 179 and that your inbound filtering/ACL rules permit established sessions with the route servers.
- Never announce the CNX peering network in a routing protocol.